Patching the VM's in azure is one of the most important task in cloud operations to treat vulnerability fixes. We have a service called "update manager" is available for the same in azure portal. An effective software update management process is necessary to maintain operational efficiency, overcome security issues, and reduce the risks of increased cyber security threats. However, because of the changing nature of technology and the continual appearance of new security threats, effective update management requires consistent and continual attention.
The basic architecture of azure update management is given below. The solution can be used to push updates for on premises and azure VM's
Let's configure update management in azure portal step by step and test the patching in a linux VM.
- The following steps highlight the actual implementation
- Create an Automation account.
- Add the Log analytics account with automation account
- Link the Automation account with the Log Analytics workspace.
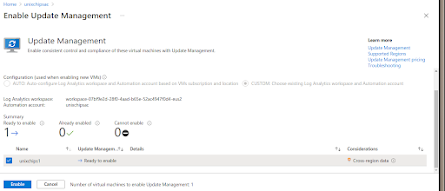
- Enable Update Management for Azure VMs.
- Add the VM's to the update manager
- Patch the VM's using update manager
Login to the azure portal and select the "automation account" from the search bar . Create the "automation account" as below . Create azure run as account is optional as it is used to manage azure resources from azure runbooks . I am keeping this as default "yes" . Please keep it in mind that name of the "Automation account" should be unique
We have succesfully created the Automation account called "unixchipsac" in the same resource group which log analytics workspace contains
Next step is to add the Log analytics workspace with the automation account . Select the Automation account which we created and go to update management , we may need a separate log analytics account for the update manager which can be created along with the update manager configuration .
So configured "update management" profile will be as below
Next step is to create a virtual machine in linux as below , i have created a virtual machine in linux named as "unixchips1" and same is available in update manager portal when we click add VM option
Now we have to patch the VM using update manager . If you click on the "missing update" tab you can see the missing updates for the particular VM.
We have to schedule the patching by providing details like deployment name, VM name, groupname ( this option is useful where we can add the machines to different groups and patch together) , pre or post scripts for patching
So we have successfully scheduled the patching window as below
After the patching if we click the jobs we can see the patching is completed successfully
If we check the Job statistics , we can see the report as below . So we have successfully patched the VM using azure update management
Thank you for Reading this blog and feel free to post your feedback and comments












No comments:
Post a Comment