What is virtual network
A Virtual Network, also known as a VNet is an isolated network within the Microsoft Azure cloud.
VNets are synonymous to AWS VPC (Virtual Private Cloud), providing a range of networking features such as the ability to customize DHCP blocks, DNS, routing, inter-VM connectivity, access control and Virtual Private Networks (VPN).
The main functions of vnet's are below
- Create a dedicated private cloud-only VNet Sometimes you don't require a cross-premises configuration for your solution. When you create a VNet, your services and VMs within your VNet can communicate directly and securely with each other in the cloud. You can still configure endpoint connections for the VMs and services that require Internet communication, as part of your solution.
- Securely extend your data center With VNets, you can build traditional site-to-site (S2S) VPNs to securely scale your datacenter capacity. S2S VPNs use IPSEC to provide a secure connection between your corporate VPN gateway and Azure.
- Enable hybrid cloud scenarios VNets give you the flexibility to support a range of hybrid cloud scenarios. You can securely connect cloud-based applications to any type of on-premises system such as mainframes and Unix systems.
Below are the key components within Microsoft Azure Virtual Networks.
SUBNETS
A subnet is a range of IP addresses in the VNet, you can divide a VNet into multiple subnets for organization and security. Additionally you can configure VNet routing tables and Network Security Groups (NSG) to a subnet
IP ADDRESSES
There are 2 types of IP addresses that can be assigned to an Azure resource - Public or Private.
There are 2 types of IP addresses that can be assigned to an Azure resource - Public or Private.
Public
- Used for internet/Azure public facing communication.
- A dynamic IP is assigned to the VM, by default. At the point the VM is started /stopped the IP is released/renewed.
- A static IP can be assigned to a VM which is only released when the VM is deleted
Private
- Used for connectivity within a VNet, and also when using a VPN gateway or ExpressRoute.
- A dynamic IP, by default, is allocated to the VM from the resources subnet via DHCP. At the point the VM is started/stopped the IP may be released/renewed based on the DHCP lease.
- A static IP can be assigned to the VM.
NETWORK SECURITY GROUPS
Network Security Groups (NSGs) allow you to permit or deny traffic (via a rule base), to either a subnet or a network interface. By default the inbound and outbound rules include an implied deny all. Finally NSGs are stateful, meaning that the TCP sequence numbers are checked in addition to, if the connection is already established.
LOADBALANCING
Azure provides three different load balancing solutions. They are,
- Azure Traffic Manager - Similar to Route53 within AWS, DNS is used to direct traffic to necessary destination. There are 3 destination selection methods - failover, performance or round robin.
- Azure Loadbalancer - Performs L4 loadbalancing within a Virtual Network. Currently only supports round robin distribution.
- Azure Application Gateway - Performs L7 loadbalancing. Supports HTTP Request based loadbalancing, SSL Termination and cookie based persistence.
ROUTING TABLES
Although Azure automates the provisioning of system routes, there may be a scenario where you need to further dictate how your traffic is routed.
Routes are applied on traffic leaving a subnet, and traffic can be sent to a next hop of either a virtual network, virtual network gateway or virtual machine.
Creating a vnet and attaching the VM's
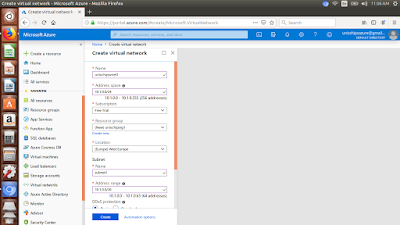
Let's create a vnet using azure portal as below
2. Provide the details including address space , resource group, subnet details etc
3. Now let's create 2 VM's in this network ( one is linux and another is windows) . Both the VM's should get the IP range of our network .Also we have enabled port 22 and 80 on the VM .
4. Let's create another VM windows with the IP of 10.1.0.5 in the same network .
5. If we try to ping to windows vm from outside using public IP we are unable to because the ICMP is blocked by windows firewall.
6. Let's enable the ICMP in windows firewall using powershell command as below
(New-NetFirewallRule -DisplayName "Allow ICMPv4-In" -Protocol ICMPv4)
\
7. And now if we try to ping to that IP we should be able to
Enabling communication between vnet's using Vnet-Vnet peer
Now we can configure the communication between the Vnet's using virtual gateway and vet peer.
1. First click on "unixvnet1 - subnets and add gateway subnet . It will automatically create the gateway IP . Here 10.1.0.64/28
2. Create a virtual network gateway for unixvnet1 as below (provide gateway type as VPN and VPN type is route typed)
3. We have to create a VPN gateway as below . select first virual network gateway as vnetgateway1 and second gateway as vnetgateway2 .
4. Create the same procedure for unixvnet2 also from step 1 to 3 and create a VM in second vnet as below . While creating VPN gateway we need to select first virtual network gateway as vnetgateway2 and second gateway as vnetgateway1. This will make sure the communication vice versa .
5. Now if we try to ping from 10.1.0.4 to 10.2.0.5 ( VM in vnet2) we can see we are able to ping
We have successfully configured two vnet's (unixchipsvnet1 & unixchipsvnet2) and established communication between two vnets using VPN gateways .
Thank you for reading



















Is it possible to earn a fortune in the merit casino? - Décor
ReplyDeleteBut the popularity of slot machines has 샌즈카지노 increased dramatically over the last 10 years, 메리트카지노 with new technology introduced to the online 인카지노 gambling industry